TL;DR
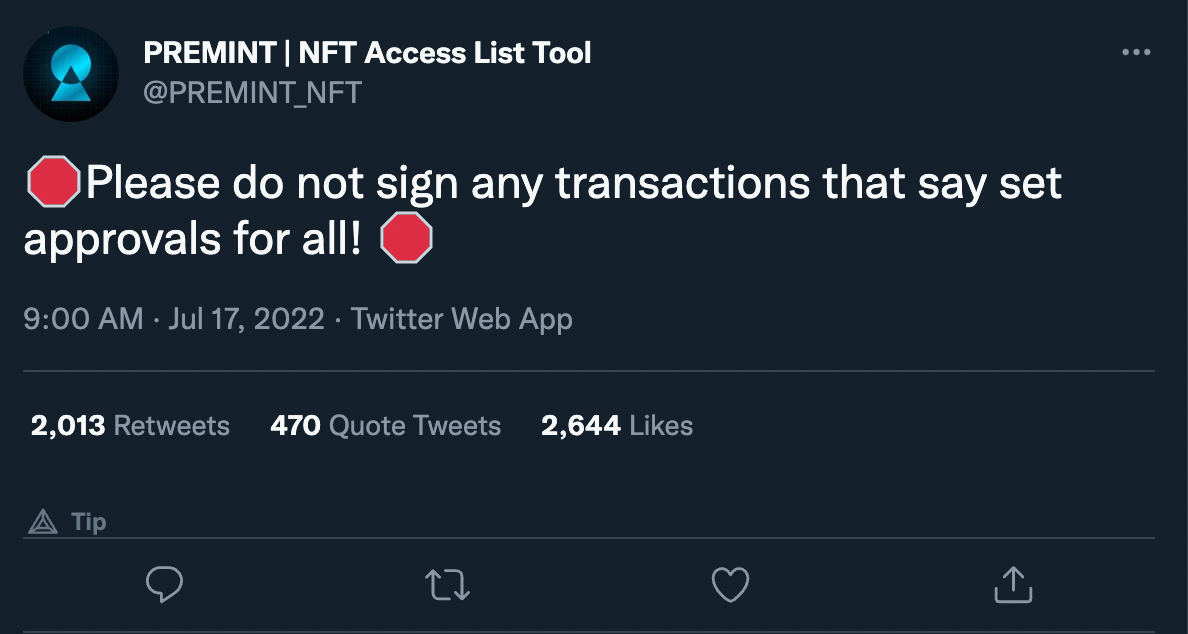
At 8:00 AM UTC, PREMINT announced on their Twitter page that their website was compromised. They advised all users to not sign any transactions requiring them to indicate “Set Approval For All” as a setting. In total, 6 exploited wallets have been identified thus far. The profits gained from the attack at this point are ~$375k, making it one of the largest NFT hacks this year.
Event Summary
A hacker uploaded malicious JavaScript code to premint.xyz, which compromised the website. The malicious code was injected into the website via URL: https://s3-redwood-labs-premint-xyz[.]com/cdn.min.js?v=1658046560357, however the file is no longer available due to the Domain Name Server no longer existing.
However, the affects of this attack on-chain are still visible. In total, six EOAs are directly associated with attack, with approximately 275 ETH (~$375k) stolen in NFT’s. The attack began at 07:25 AM UTC.
On-Chain Analysis
A total of 6 primary EOAs have been found that are associated with this attack:
-
0x28733…
-
0x0C979…
-
0x4eD07…
-
0x4499b…
-
0x99AeB…
-
0xAAb00…
The first two wallets, 0x0C979… and 0x28733… began seeing stolen NFTs being transferred in at 07:25 AM UTC. It is suspected that the malicious code was injected into premint.xyz at this time. The two wallets contain NFTS such Bored Ape Yacht Club, Otherside, Oddities and goblintown.wtf, et al, were compromised. These wallets were located by utilizing Social Media sites and cross-referencing announcements of stolen NFTs with blockchain activity.
For example, the Twitter post below shows a user claim that 2 Goblintown NFTs were stolen from the Premint exploit:
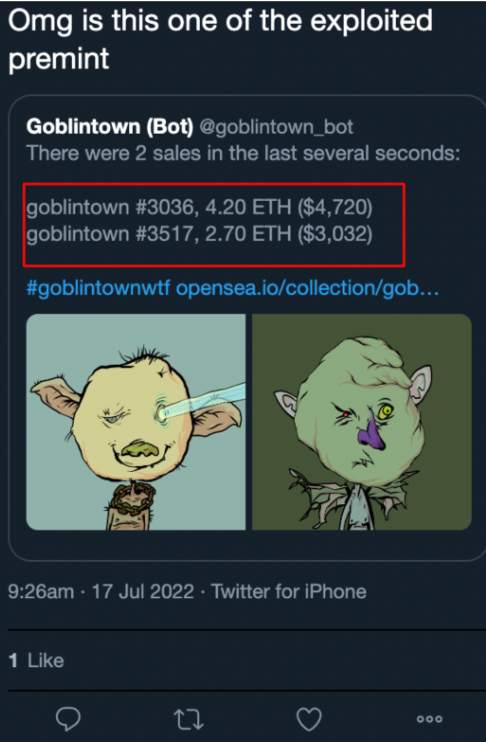
The blockchain can be checked from here. By searching for the two NFTs on OpenSea via their token ID, it can be seen how they’ve been traded. From there, the blockchain can be searched to find the wallet that stole the NFTs. Which in this case is EOA 0x0C979…
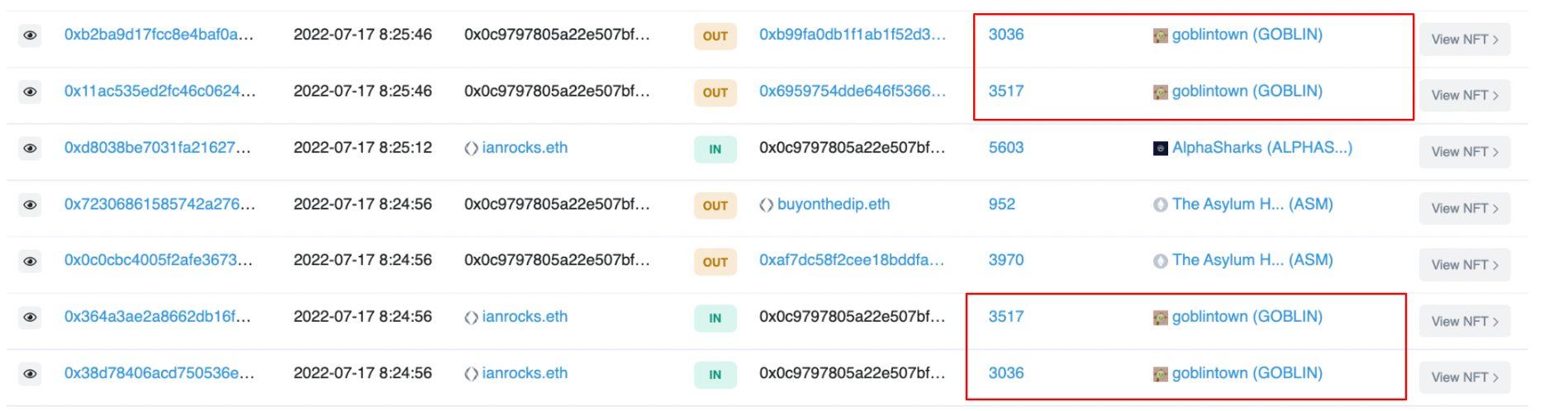
When examining the incoming and outgoing of NFT’s in this wallet, the typical patterns that are seen in Discord phishing hacks can be seen here; a large inflow of assets, followed by a quick sell-off. The first transaction into this wallet comes from 0xAAb00F… which also funded 0x28733…
It can be confirmed that 0x28733… is also involved in the hack by repeating the above process. One victim in the attack posted that they lost their Moonbirds Oddities.
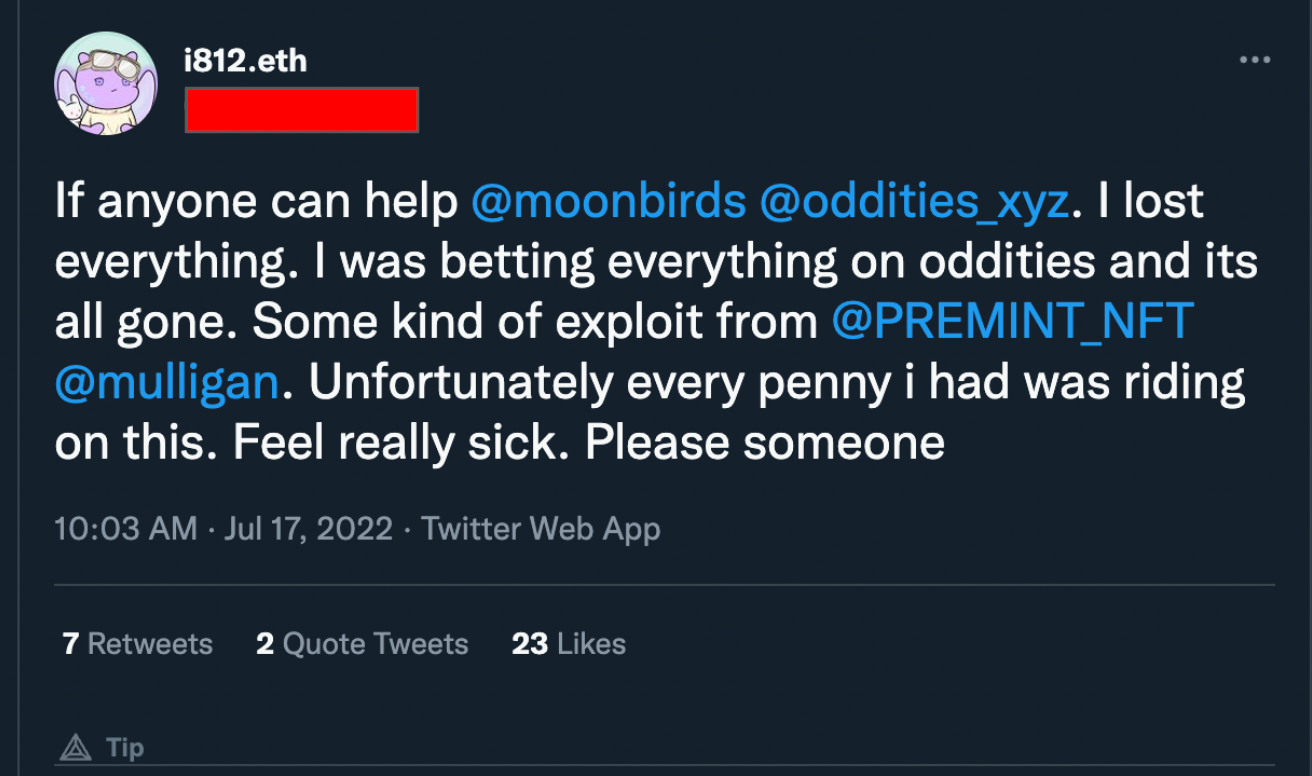
The username is in a ENS format, and when searching for it on Etherscan there is an outflow of Moonbird NFTs to EOA 0x28733… which confirm the post.
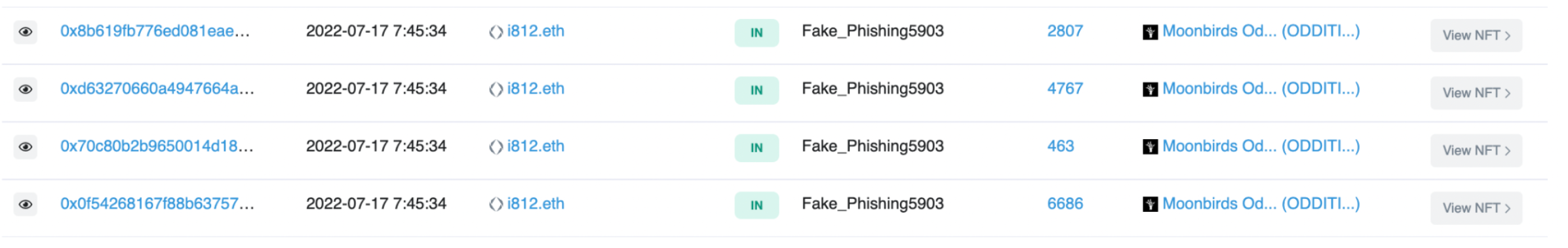
When analyzing the rest of the activity in this wallet, it follows the same pattern as EOA 0x0C979…, a large inflow followed by a quick outflow.
In total, both wallets stole 314 NFTs including BAYC, Otherside, Globlintownm et al. In total, ~275 ETH was lost in the attack amounting to $374,417.66, making it one of the largest NFT hacks this year.
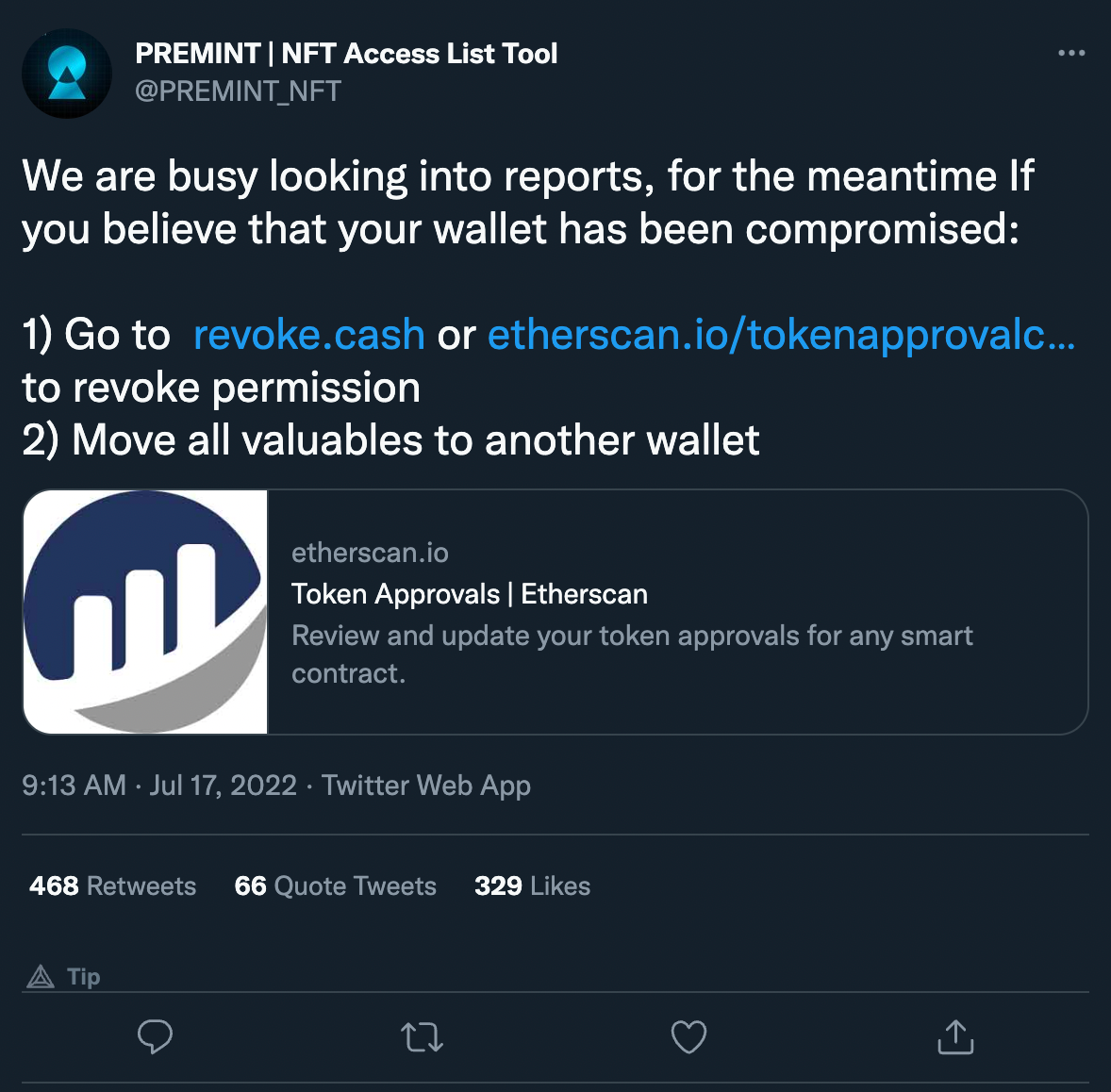
As Premint realized the breach, they put out a tweet warning users that their website had been compromised and advised users to use Revoke.Cash if they believe they were affected by the site.
This looks to have paid dividends, as two more wallets were identified as exploiter EOAs:
-
0x4eD07
-
0x4499b
However, both wallets had transactions reverted as users of Premint recognized an attack and took action:
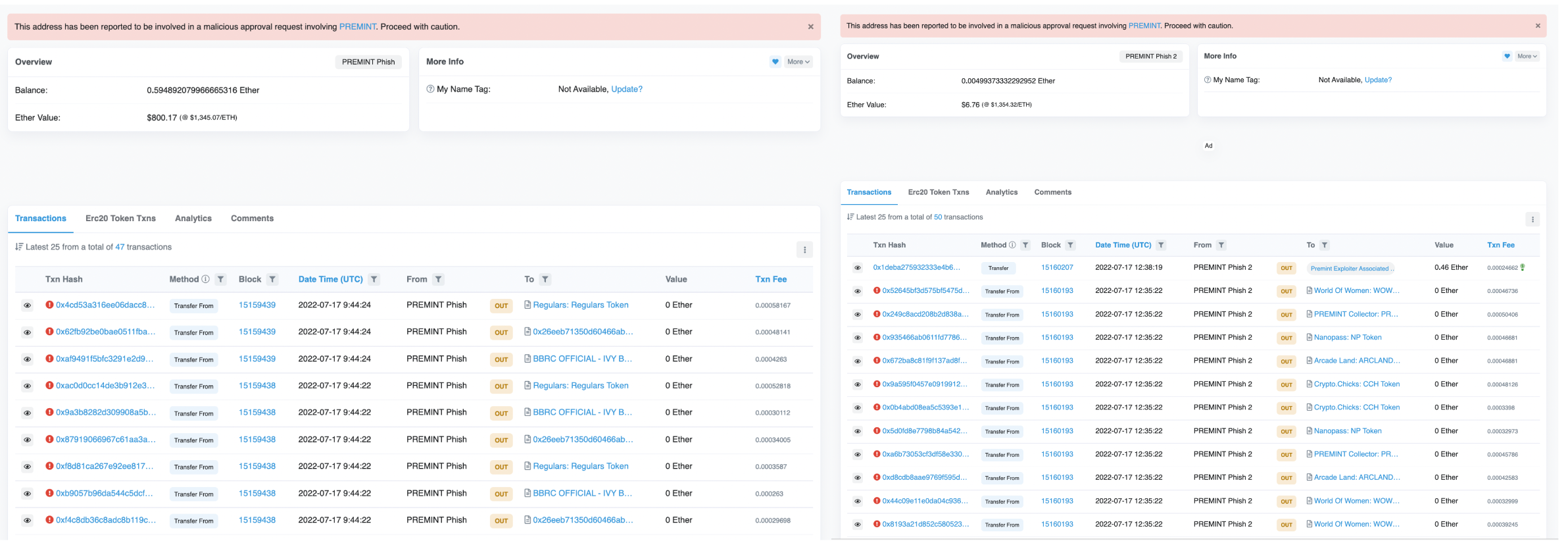
Some of the profits from the successful attacks have been transferred to EOA 0x99Ae… totalling 256.5 WETH from 0x0C979… and 0x28733. A further 16.4 ETH was also transferred into this wallet from EOA 0xAAb0… which funded exploiter wallets and was also sent profits from the attack.
Unfortunately, it is likely that the funds will make their way through Tornado.Cash.
Another Example of Web2 Vulnerability Affecting Web3
Web2 has been the predominant state of the internet with its emphasis on social networking and user-generated content. Users turn to Web2 for its ease of use when making investments in NFT and cryptocurrency. However, Web2 infrastructure often involves a single point of failure through centralization vulnerabilities. This shows how one compromise can lead to devastating losses for the NFT community.
An example would be a phishing attack that took place in June this year on The Bored Ape Yacht Club NFT (BAYC). The Discord account of Boris Vagner, the community manager, was compromised, resulting in an attacker posting fake links on the official Discord channels of a fake BAYC website targeting Bored Ape and Otherside holders. The attacker was able to profit ~$319k from stolen NFT’s.
A second example would be when NFT artist Beeple’s Twitter account was compromised, leading to his followers losing ~$438k worth of NFT and cryptocurrency. In the first attack, the hacker tweeted out a collaboration link to followers which led to users being drained of around $73k. A second attack followed and drained the followers' wallets of cryptocurrency and NFTs, adding to the total ~$438k lost in the scam.
These attacks are indicative of how vulnerable Web2 can be regarding Centralization issues.
Reference
Hackers swipe $360,000 worth of Bored Ape Yacht Club NFTs in the 3rd attack on Yuga Labs since April
Twitter Hacks on the Rise - Blog - CertiK Security Leaderboard
Bored Ape Yacht Club Discord Hit With Phishing Attack - Blog - CertiK Security Leaderboard



