TL;DR
On 11 July 2022, an attack that impersonated Uniswap occurred, resulting in the exploiter gaining 3,278 ETH (~ $3.6M) and 240 WBTC (~ $4.7M) from Positions NFTs in a phishing campaign.
Event Summary
The phishing attack started with the creation of a fake LP token called ‘UniswapLP[.]com’. The exploiter spent 8.5 ETH airdropping this fake token to ~74k wallets using a fake link, some targeting big names in the crypto community like Vitalik Buterin and Justin Sun. Once users discovered the tokens had been airdropped and were baited to look at the website in the token name, they were greeted with a rewards claim. Users would be entitled to claim a number of UNI tokens, equivalent to the UniswapLP they had been airdropped.
The phishing wallet 0x09b… gained 3,278 ETH (~ $3.6M) and 240 WBTC (~ $4.7M) from Uniswap V3: Positions NFT from the phishing attack. The exploiter swapped 240 WBTC for 4,295 ETH for a combined total of ~7,573 ETH. The exploiter then transferred 7,500 ETH to Tornado Cash, leaving 70.98 ETH in the wallet.
Attack Technical Analysis
The attacker created a fake ‘UniswapLP[.]com’ token, contract address 0xCf3…, which was then airdropped to ~74k wallets, each receiving 400 tokens.
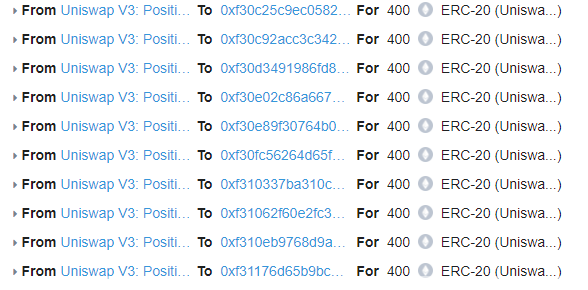
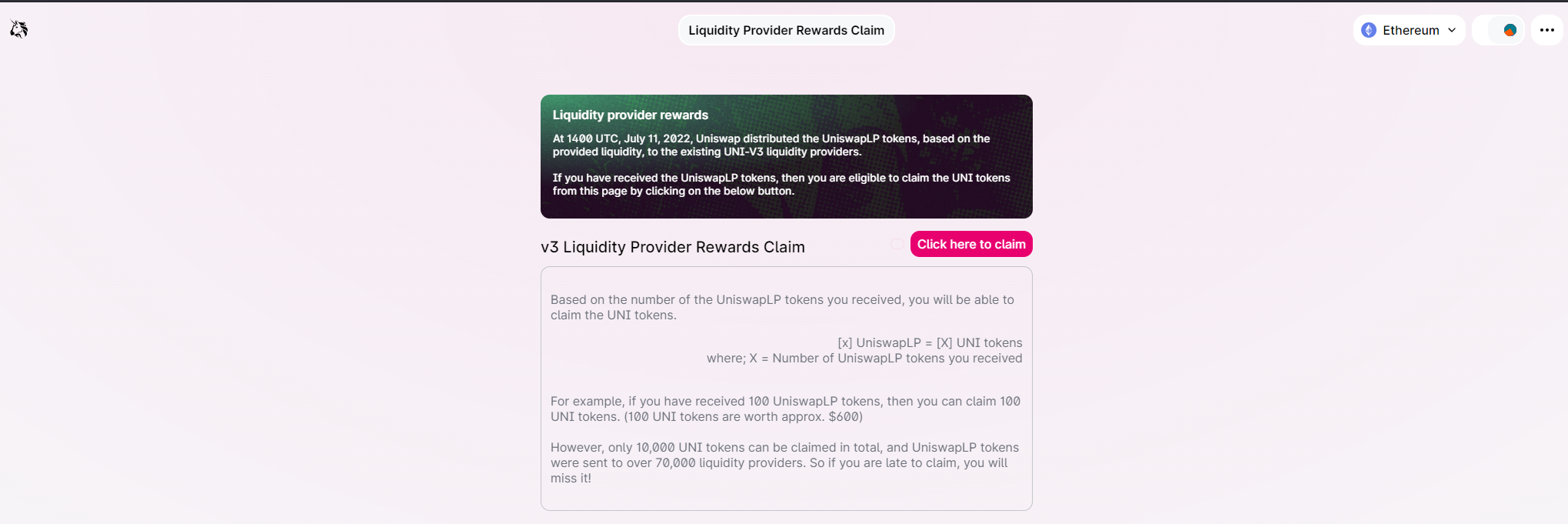
When a user navigated to the phishing site in the contract name, they received a message stating they were able to claim UNI tokens equivalent to the number of UniswapLP tokens they received.
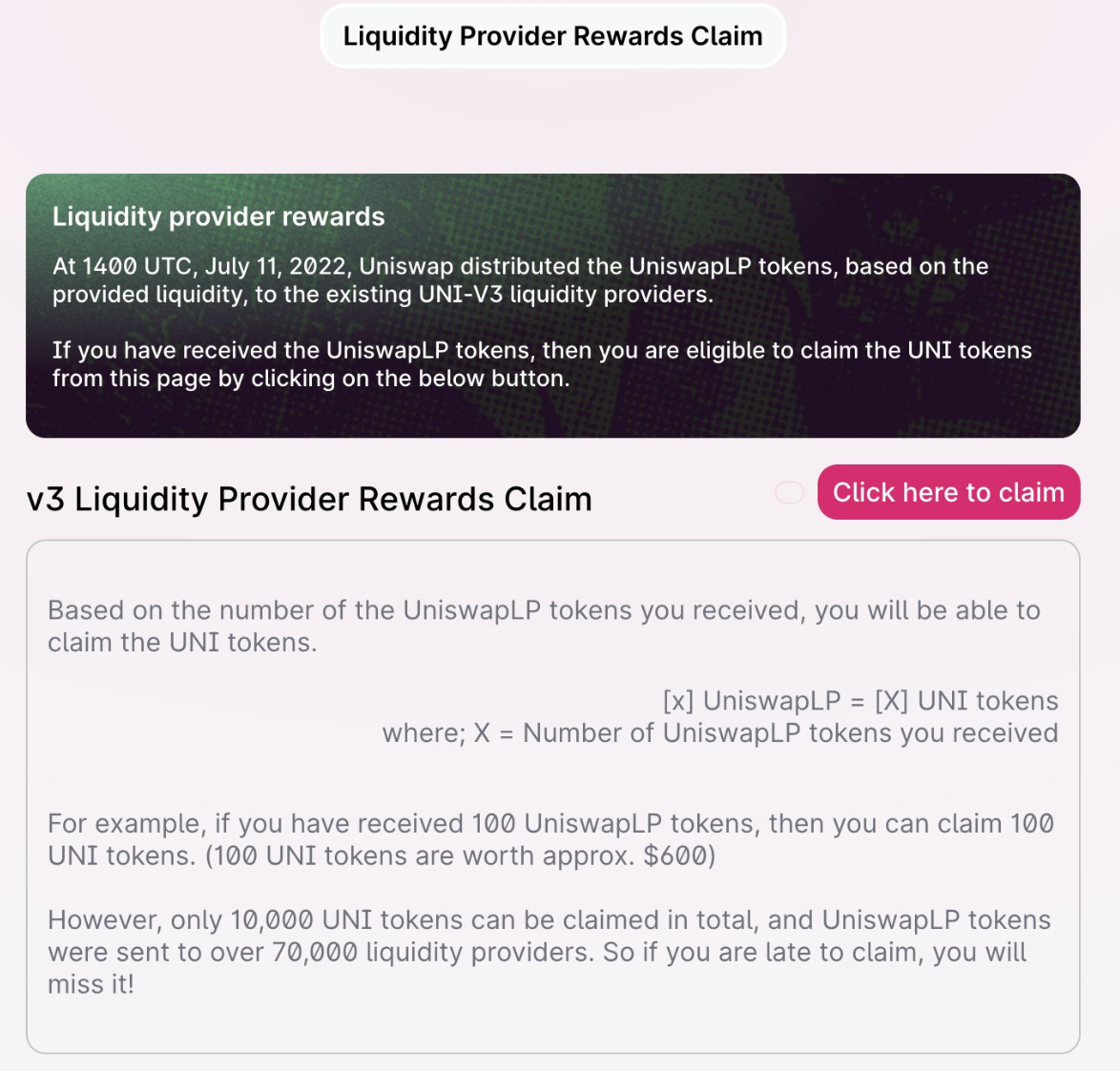
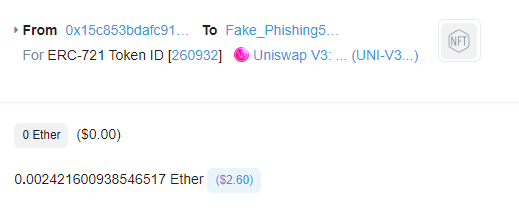
Once a user clicked on the ‘Click here to claim’ button and approved their wallet, they invoked a function called SetApprovalForAll(). This function gave the exploiter approval to access the user’s wallet, which enabled the exploiters to steal a user’s Positions NFT. The exploiter is now able to interact with the Uniswap V3: Positions NFT contract and swap the NFTs for WBTC and ETH.
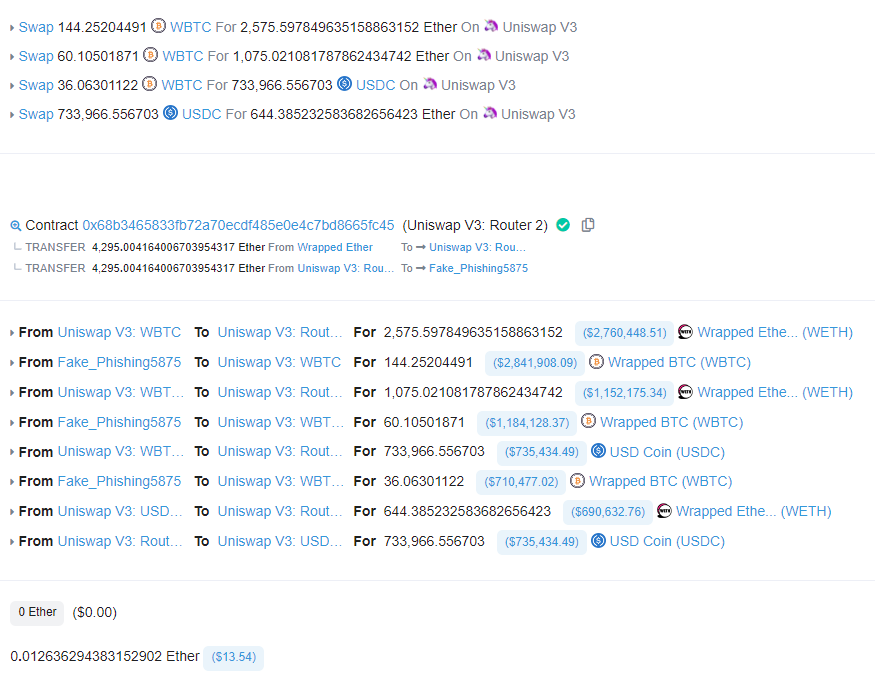
Here is one of the exploit transactions in which the exploiter collects 198 WBTC and 2,389 ETH:
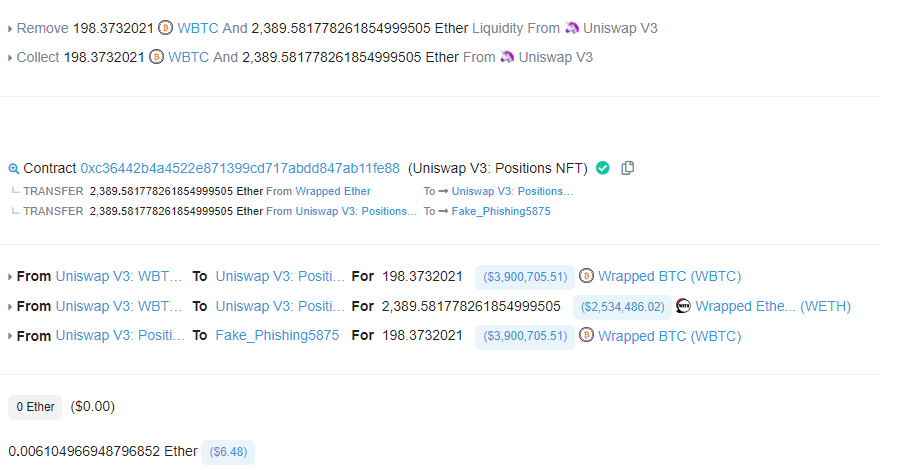
There are a further 3 similar transactions with a combined total of 240 WBTC and 3,278 ETH.
The 240 WBTC is then swapped for 4,295 ETH.
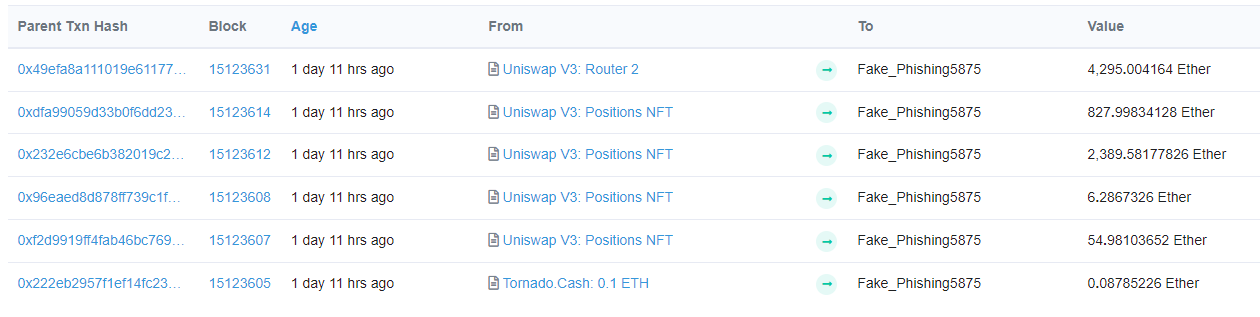
Looking at the internal transactions tab on the wallet we get a simplified view of the ETH gained by the exploiter.
Phishing Site
By looking at the phishing site, it can be seen that it’s designed to imitate the Uniswap app:
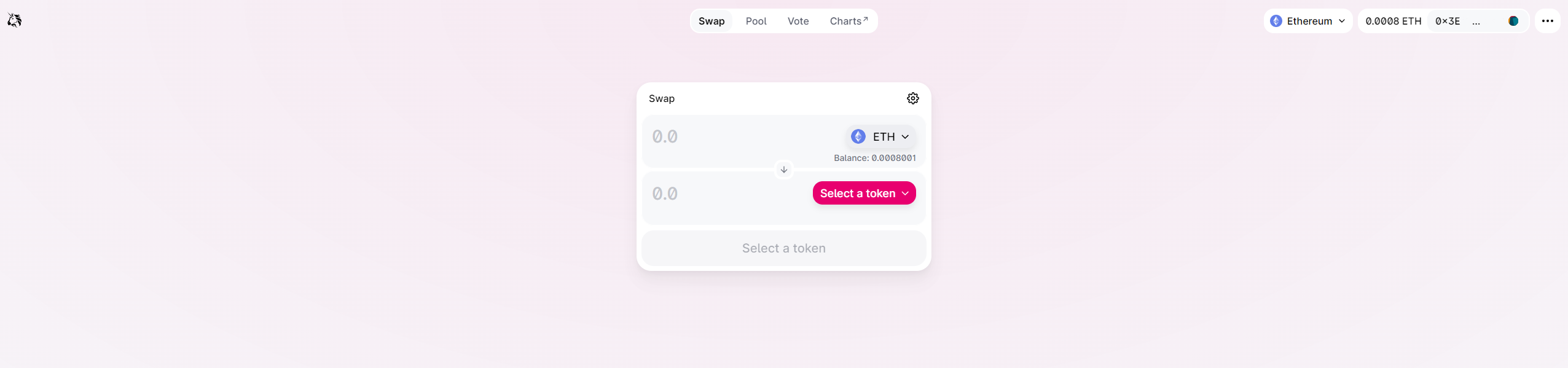
There are a couple of key differences, however. Uniswap correctly displays the connected wallet address, while on the other hand, the hamburger icon on the phishing site doesn’t work, nor does the network selection. A quick check of whether a website is working correctly is a great protection strategy to avoid being involved in scams.
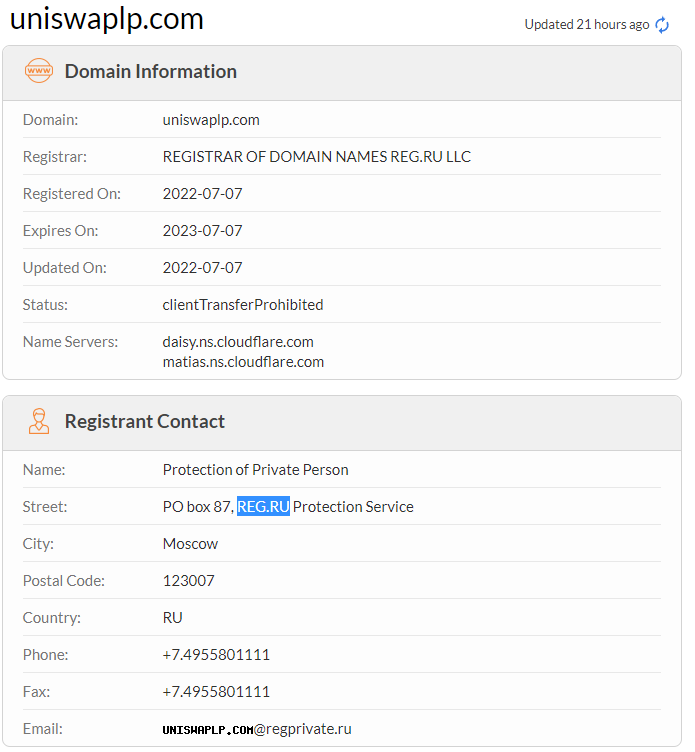
Checking UniswapLP[.]com in WHOIS shows that the site was only registered on 7 July, 4 days prior to the attack, and registered with REG.RU. Registering a website requires a user to provide personal details. REG.RU is a Russian registry company based in Moscow, that provides anonymous website registration. All the details in the Registrant Contact box belong to REG.RU and the real registrant remains anonymous.
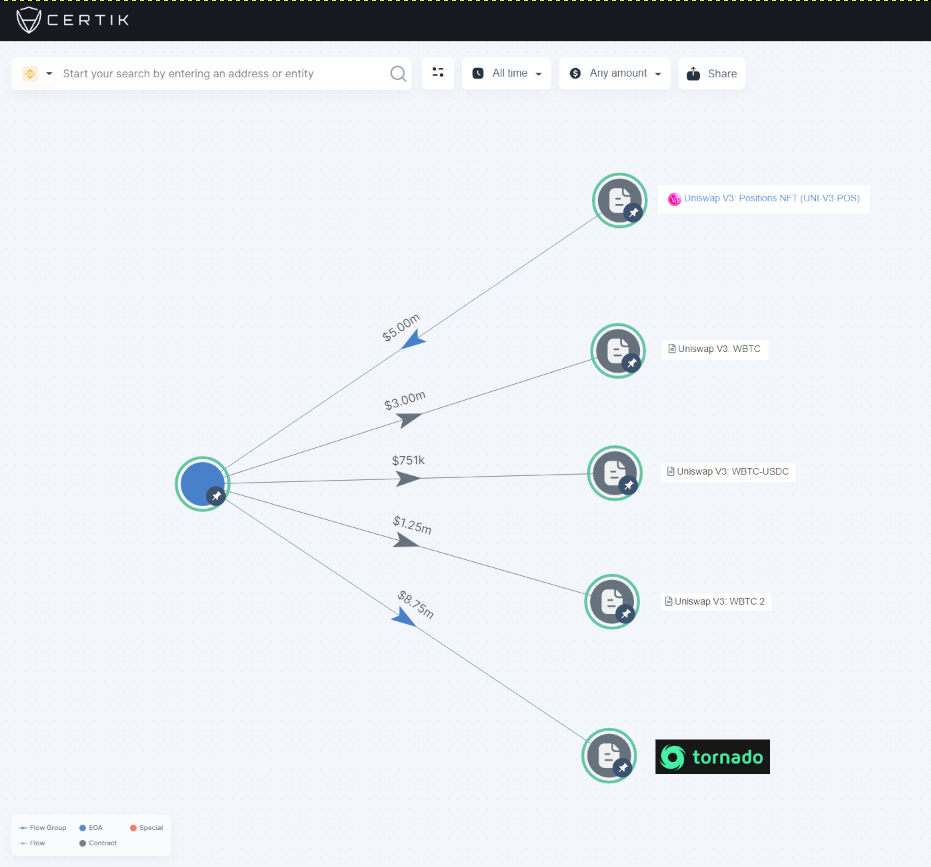
Profit and assets tracing
Using Skytrace, there is a better view of the funds that were taken and the interactions with Uniswap contracts. In this phishing attack, a total of 7,500 ETH was routed to Tornado Cash, ~$8.7M at the time of transferring.
Conclusion
This phishing campaign saw exploiters net a staggering 7,573 ETH ($8.7M). The exploit highlights the need to identify imposter accounts from real ones. By posing as Uniswap, this exploiter was able to exploit the unknowing and profit a massive amount of ETH. Often these accounts will replace a single character or add an additional character to their names which are otherwise identical to the original account. It is paramount to remain vigilant when approaching any announcement, direct message, and link to investigate for legitimacy.
References
https://cointelegraph.com/news/more-than-4-7m-stolen-in-uniswap-fake-token-phishing-attack
https://twitter.com/sniko_/status/1546535668247060481?s=20&t=sKV7dJlpSebruximO8s-OQ
https://twitter.com/i/web/status/1546631971626958848
https://twitter.com/sniko_/status/1546535673661997058?s=20&t=sKV7dJlpSebruximO8s-OQ
https://twitter.com/cz_binance/status/1546848347100700676?s=20&t=NBqBQ_PoIfdGv5H45ZqIKw
https://twitter.com/samczsun/status/1546629148637929472?s=20&t=1kRV9Sq0fRoBbOVxj2Nduw
https://twitter.com/ethersole/status/1546629065645359106?s=20&t=1kRV9Sq0fRoBbOVxj2Nduw



