TL;DR
On March 9 2022, at 01:50:20 PM +UTC, Fantasm Finance collateral reserve pool was exploited for ~$2.62M. The attacker was able to mint more XFTM tokens than anticipated and swapped all of the tokens to ETH sing privacy protocol Tornado Cash.
Event Summary
On March 9 2022, Fantasm Finance announced on their Twitter that their collateral reserve had been exploited Fantastic Protocol on Twitter. Fantasm Finance is a DeFi project aimed at developing synthetic tokens for the Fantom ecosystem. FTM is Fantom’s native token and one of the tokens used as collateral backing on Fantasm.
The Fantasm Finance hack took advantage of a flaw in the error-checking code of the protocol’s mint function. The attacker was able to exploit this code by performing a transaction that sent only FSM tokens (which are used as collateral in minting) and no FTM tokens. The incorrect error checking code permitted the transaction, allowing the attacker to mint XFTM tokens without depositing any FTM. The hacker was able to mint XFTM, a representation of Fantom’s FTM on Fantasm, by using a small amount of Fantasm’s FSM tokens. The hackers started with 50 FTM, gradually using larger amounts to swap over 2.8 million XFTM in total. The stolen funds were then swapped for over 1,007 ETH or about $2.62 million through Tornado Cash.
All of the funds in the pool were withdrawn using the same method by the deployer, which Fantasm developers said in a follow-up tweet that some of the FTM collateral was “white hacked”. They also announced that they would compensate those affected by the exploit by distributing the accumulated FTM fee to FSM stakers and lockers.
Fantasm Finance posted a postmortem that can be found: Fantasm Finance Post Mortem: Exploit 09 March 2022
Attack Technical Analysis
According to FTM’s post mortem the attack went as follow:
BNB Chain
- The Exploiter received funds from BNB Chain via Tornado Cash:
-
The Exploiter swapped BNB to USDC via Pancakeswap: 0xe47bd
-
The Exploiter bridged USDC to Fantom via Celer Bridge: 0x2b5f6
Fantom Chain
-
The Exploiter received USDC from Celer Bridge: 0x39be0
-
The Exploiter received FTM from a faucet: 0x455f7
-
The Exploiter swapped USDC for more FTM: 0xed819
-
The Exploiter deployed a contract (0x944b58…) which will trigger the exploit: 0x944b5That contract exploited the error in Fantasm’s Pool contract where the developer missed the condition checking for the minimum amount of input FTM when minting XFTM.
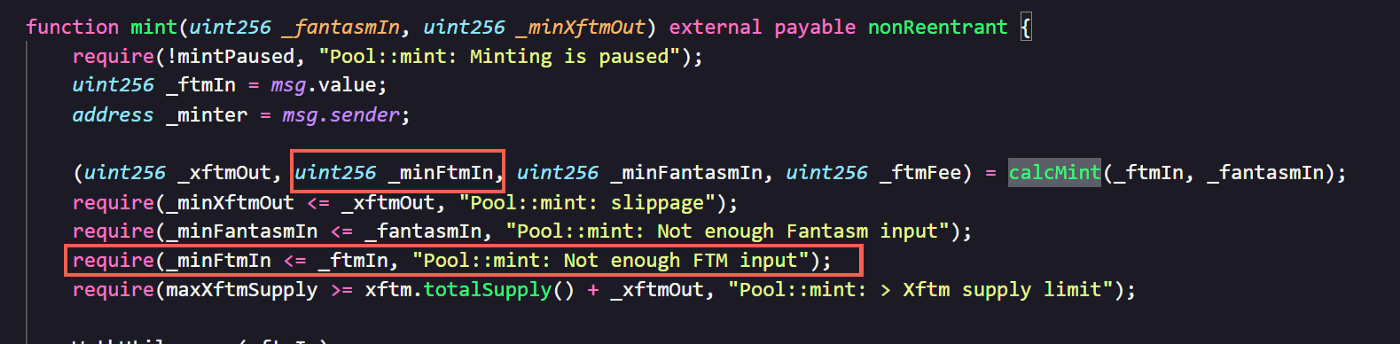
-
This contract deployed by Exploiter repeatedly performed the following: i. Mint XFTM by input only FSM token without entering any FTM ii. Collect XFTM token iii. Sell XFTM token to FTM iv. Buy more FSM and repeat the first step to get a larger amount of FTM
-
Eventually, the exploiter sold all FTM for ETH and bridged these ETH to Ethereum, again via Celer Bridge. The total amount exploited is 1008.498875252390151 ETH (approximately $2,622,097)
Ethereum Chain
- The Exploiter used Tornado to siphon the stolen fund: 0x47091
__In short the analysis shows that: __
-
The attacker deployed an unverified contract at address 0x944b5.
-
In the first transaction, the attacker swapped the Fantom token(FTM) to FSM token and called mint() function in contract 0x88067.
-
The attacker called collect() function and collected more XFTM token than was intended.
-
The attacker repeated step 2 and 3 several times to gain huge profit.
Contract Vulnerability Analysis
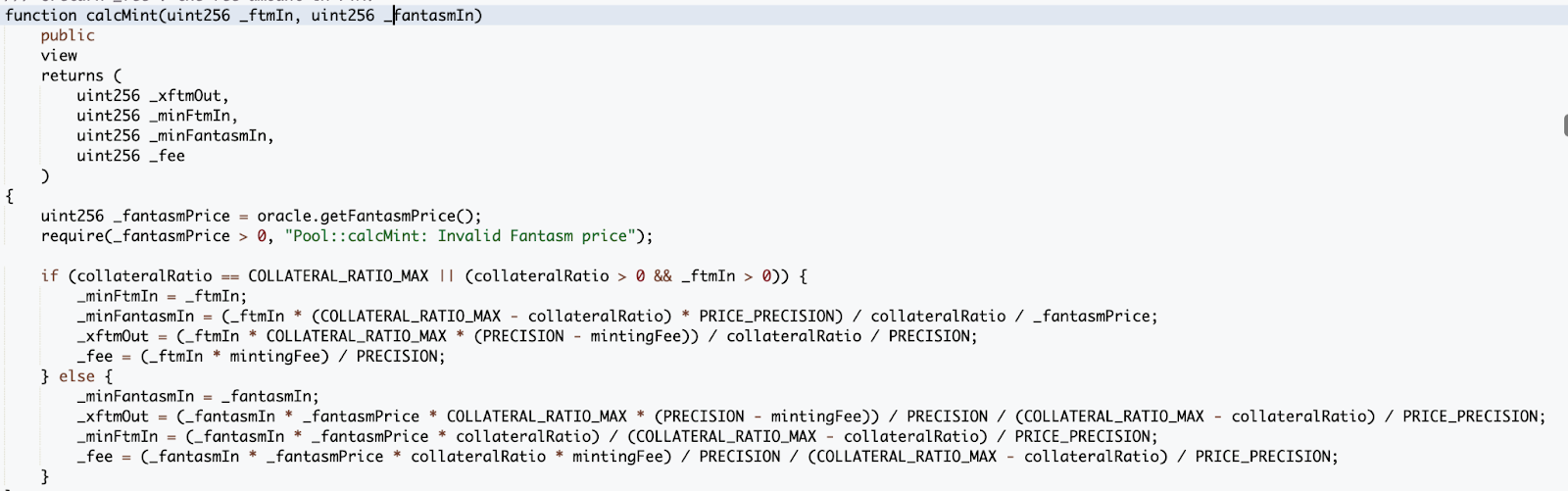 In function calcMint, the contract uses the following formula to calculate the mint amount:_xftmOut = (_fantasmIn * _fantasmPrice * COLLATERAL_RATIO_MAX * (PRECISION - mintingFee)) / PRECISION / (COLLATERAL_RATIO_MAX - collateralRatio) / PRICE_PRECISION;
In function calcMint, the contract uses the following formula to calculate the mint amount:_xftmOut = (_fantasmIn * _fantasmPrice * COLLATERAL_RATIO_MAX * (PRECISION - mintingFee)) / PRECISION / (COLLATERAL_RATIO_MAX - collateralRatio) / PRICE_PRECISION;
Due to the decimal error, the _xftmOut is bigger than it is supposed to be.
Profit and assets tracing
The attacker gained about 1000 ETH and all the funds were transferred to Etherscan (address 0x47091) and sent to tornado proxy.
Conclusion:
The Fantasm Finance exploit was made possible by incorrect error checking code within the project’s smart contract. Overall, the attacker was able to mint XFM tokens for a fraction of their true value and sell them back to drain value from the project. Amid news of the hack, the value of the XFTM token fell by 82.28% 24 hours after the exploit.




