TL;DR
On 10 December, 2022 at 1:21:34 AM UTC, Mu Coin was flash loan attacked for approximately 45 ETH ($57K) on AVAX. The attack took advantage of differences in price between the token in the LP pools and the token price obtained by buying bonds, resulting in a smart contract that is vulnerable to economic arbitrage. Mu coin founder Jon Vaughn acknowledged the attack and is attempting to raise the price back to levels similar before the incident.
Summary
On 10 December, 2022 at 1:21:34 AM UTC, our CertiK Skynet system noticed a suspicious flash loan on AVAX. After further investigation, CertiK analysts confirmed it to be a price manipulation attack. The attacker gained 57,659 USDC which they then swapped to 45.1 ETH and sent to cBridge followed by Tornado Cash.
This is a good example of an oracle manipulation attack. This system of contracts forms a bond system that allows user’s to exchange USDC for equivalent tokens. However, it is vulnerable to flash loan attacks as the bonds are based on a single pair of LP pools defined by both Mu coin/Mu Gold and Mu coin/USDC.
This type of attack usually occurs as follows:
- The attacker takes out a flash loan of Mu/USDC pool
- The attacker calls the function mu_bond(), this mints Mu Coin to the attacker who provides USDC to begin the process
- They then call the function mu_gold_bond(), this Mints Mu gold to the attacker, again, providing USDC to do so
- The attacker returns USDC and uses new Mu Coin and Mu Dold to arbitrage the pools for USDC
Below is the pattern of transfers used to see how the attacker withdrew Mu Coin and Mu Gold using USDC to pay for it. Essentially the attacker bought cheaper Mu Coin and Mu Gold then used it to arbitrage the pools.

Following the attack, Mu Coin founder Jon Vaughn addressed the attack via the official Discord server. He begins with stating that he “Made a huge blunder.”

Vaughn is still active in Discord and trying to recover the project, citing he, “learned a valuable lesson,” from the incident. The recovery will not be easy as, at the time of writing, token Mu Gold (MUG) is down 94% and Mu Coin (MU) is down 84%. Nevertheless, the project remains active and seeks to recapture the momentum it lost.
Exploit Transaction
https://snowtrace.io/tx/0xab39a17cdc200c812ecbb05aead6e6f574712170eafbd73736b053b168555680
Money laundering Transactions:
Swapped to 45.1 ETH: 0x864b6
Sent to cBridge: 0x03257b
Sent to Tornado Cash:
- 0x03782d
- 0x5efa44
- 0x4c7ec3
- 0xc4bc44
- 0x9c957d
- 0xd73bec
- 0xd20b2d
- 0x35ab22
- 0xf72eed
- 0x85292c
Relevant Addresses
Attacker: 0xd46b4
Attacker contract: 0xe6c17
Victim contract (MuBank): 0x4aa679402c6afce1e0f7eb99ca4f09a30ce228ab
Pair 1 MUG-MU Pair (Flash loaned): 0x67d9aab77beda392b1ed0276e70598bf2a22945d
Pair 2 MU- USDC Pair (Swapped for): 0xfacb3892f9a8d55eb50fdeee00f2b3fa8a85ded5
ERC20 Tokens:
- Mu Coin - 0xd036414fa2bcbb802691491e323bff1348c5f4ba
- USDC coin - 0xa7d7079b0fead91f3e65f86e8915cb59c1a4c664
- Mu Gold - 0xa7d7079b0fead91f3e65f86e8915cb59c1a4c664
Attack Flow
- The attacker began by flash loaning 578,987 MU coin tokens from Pair 1 (Trader Joe MUG-MU)
- The attacker then swaps 578,000 MU tokens for 85,000 USDC on Pair 2
- The attacker then swaps the money into the victim contract. The prices of MU and MUG on the victim contract is reliant on Pair 1 and Pair 2, thus the attacker can get more tokens. a. The attacker contract then calls mu_bond() to swap 3,300 USDC to 99,102 MU b. The attacker contract calls mu_gold_bond() to swap 6,990 USDC to 9,640 MUG
- Attacker contract inputs 3,300,000,000,000,000 (3,300 USDC)
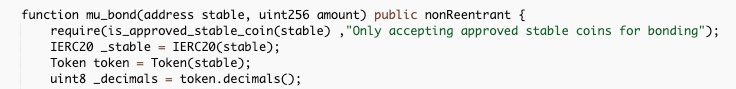 a. The price is directly based off the router, before the attack the ratio was roughly 1.5x versus a bond. The exploiter calls sync() to force the price. The flash loan disrupted the price of the pool and the exploiter was able to get 30x the valuation on their loan. As a result they were able to transfer 3300 USDC into 99,000 tokens.
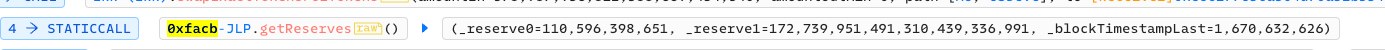
b. Before the flash loan, the reserves were stocked as follows:
a. The price is directly based off the router, before the attack the ratio was roughly 1.5x versus a bond. The exploiter calls sync() to force the price. The flash loan disrupted the price of the pool and the exploiter was able to get 30x the valuation on their loan. As a result they were able to transfer 3300 USDC into 99,000 tokens.
b. Before the flash loan, the reserves were stocked as follows:
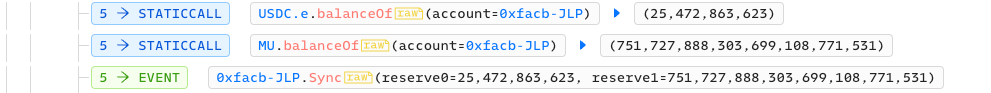
 c. Afterward:
c. Afterward:
- The exploiter then takes a bond on the other pair contract using mu_gold_bond() and repeats the same exact steps.
- In both cases the attack obtained more than 98 percent of both the Mu Coin and Mu Gold.
- This allowed the attacker to arbitrage the USDC out of the Mu/USDC pool.
Contract Vulnerability
There is a pricing issue between the token price in the LP pools versus the token price obtained by buying bonds. As a result, the contract is vulnerable to arbitrage and is inherently an economic and smart contract design issue.
Profit and Assets Tracing
The attacker took 57,659 USDC, swapped it for 45.1 ETH, and then sent it to cBridge in the following transaction.

All 45.1 ETH were eventually transferred to Tornado Cash, a digital asset obfuscation service.

Conclusion
The Mu Coin incident may be a recent incident however the impact can already be seen top-down throughout the project. This incident has been a set back for the development of the project as it appears to negatively impacted the founder’s invested asset profile in the project. The founder has deemed this to be a, ‘100K blunder'. Fortunately for the project, user assets appear to be intact but the slippage in price for both $MU and $MUG no doubt caused fear, uncertainty, and doubt in the community. For being a smaller project, the community remains active and the founders and developers interact on a daily basis. Strong community is key to strong recovery and within the Web3 ecosystem we are all apart of the community at large. Our goal at CertiK is to foster a safer and stronger community for all. With smart contract auditing you can secure your own project’s spot in the web3 community. Get audited today at certik.com!

 a. The price is directly based off the router, before the attack the ratio was roughly 1.5x versus a bond. The exploiter calls sync() to force the price. The flash loan disrupted the price of the pool and the exploiter was able to get 30x the valuation on their loan. As a result they were able to transfer 3300 USDC into 99,000 tokens.
b. Before the flash loan, the reserves were stocked as follows:
a. The price is directly based off the router, before the attack the ratio was roughly 1.5x versus a bond. The exploiter calls sync() to force the price. The flash loan disrupted the price of the pool and the exploiter was able to get 30x the valuation on their loan. As a result they were able to transfer 3300 USDC into 99,000 tokens.
b. Before the flash loan, the reserves were stocked as follows:
 c. Afterward:
c. Afterward:



