TL;DR
On 13 January, 2023 the multi-chain lending protocol LendHub announced on their Twitter account that they had suffered an exploit on 12 January resulting in the loss of approximately $6 million. The exploiter took advantage of a discrepancy between a retired IBSV cToken and a new token, where the former had not been removed from the protocol's old market despite no longer being in use.
Summary
LendHub announced on their Twitter account that they experienced an exploit leading to the loss of approximately $6 million. LendHub is a multi-chain decentralized secure lending platform that operates on Binance Smart Chain (BSC) and Huobi Eco Chain (HECO).
The vulnerability, that allowed the exploiter to take advantage of the contracts, likely stems from the fact that the old and new IBSV tokens exist simultaneously in the market, with both taking their price from the new IBSV. The exploiter obtained old IBSV tokens by depositing HBSV tokens, borrowing assets from the new market, then redeemed HBSV back in the old market.
The incident led to the Total Value Locked (TVL) of LendHub to drop from $6 million to $90,305.
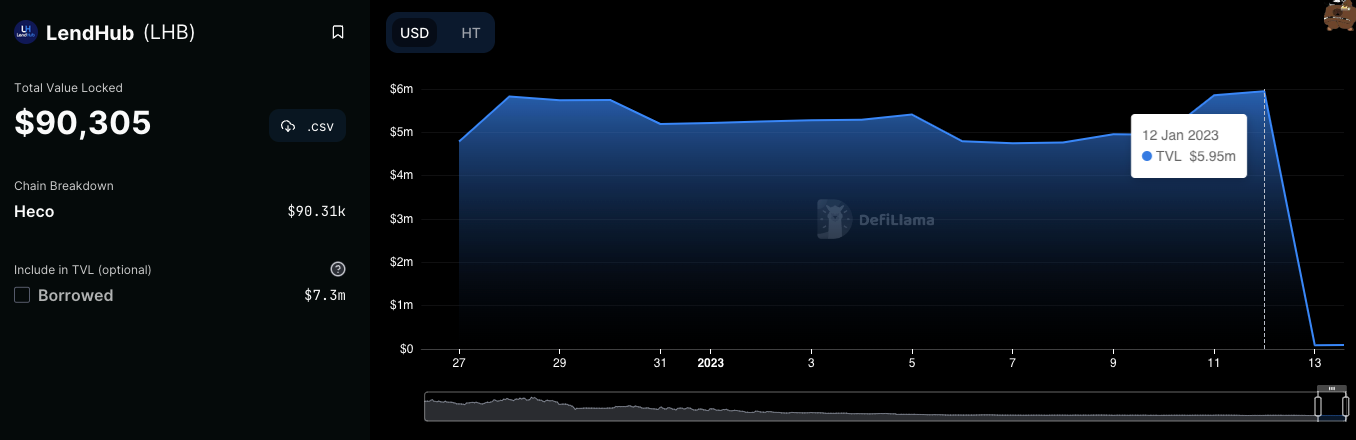 Chart: LendHub TVL drop following the exploit.
Chart: LendHub TVL drop following the exploit.
Since all contracts on HECO involved in this incident are unverified and the previous states of the contract configurations are unknown, the following analysis is based on what we are able to determine from the open source github repo and transaction histories. The analysis is not definite and further clarification from the Lendhub team is required to confirm the vulnerability.
Attack Flow
- On 11 Jan, 2023, at 10:11 PM +UTC, the exploiter received 100 ether (ETH) from Tornado Cash on Ethereum.
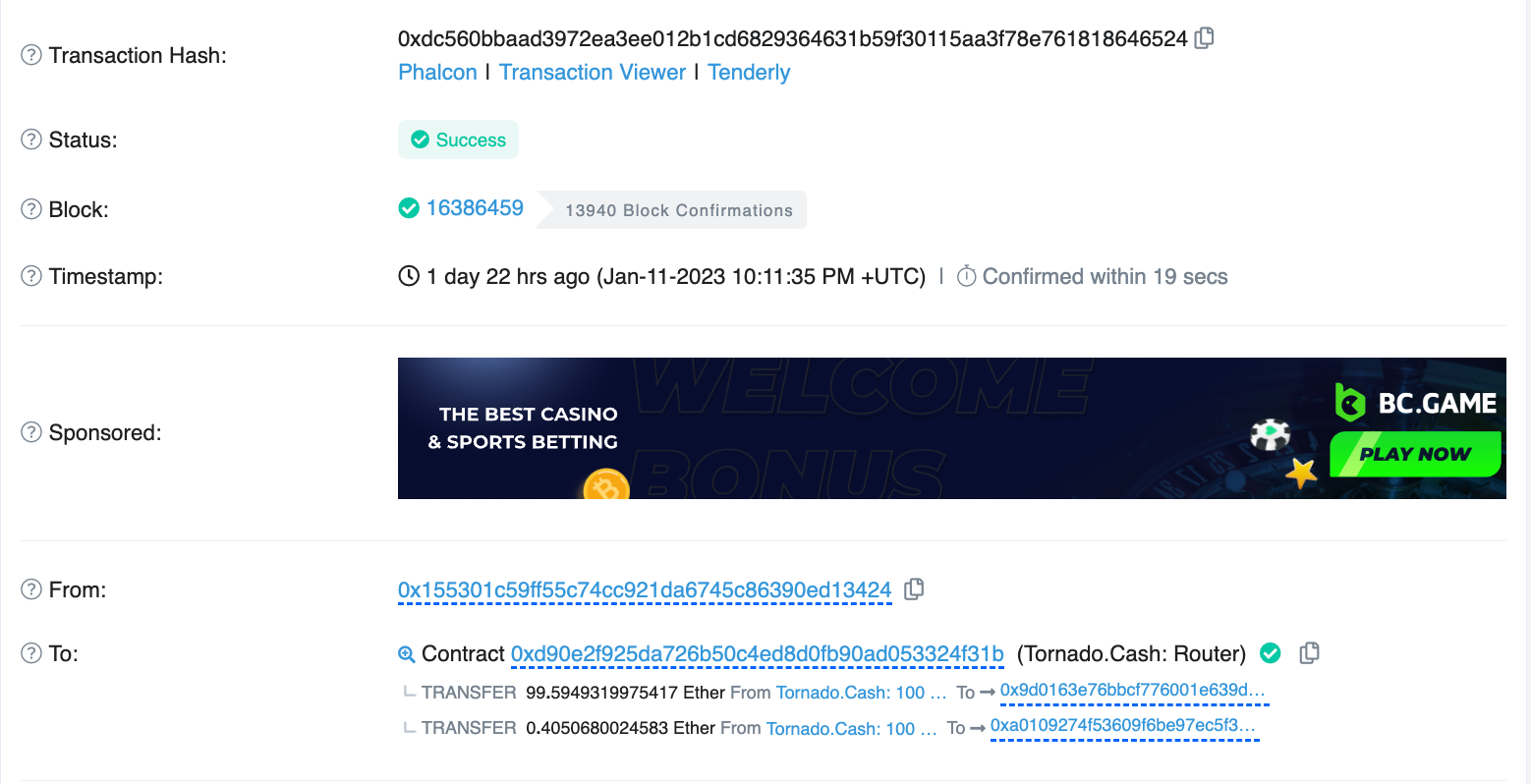 Image: Exploiter receiving ETH from Tornado Cash. Source: Etherscan
Image: Exploiter receiving ETH from Tornado Cash. Source: Etherscan
- The exploiter then swapped ETH for Heco Token (HT) and USDT and transferred tokens cross-chain to the HECO chain.
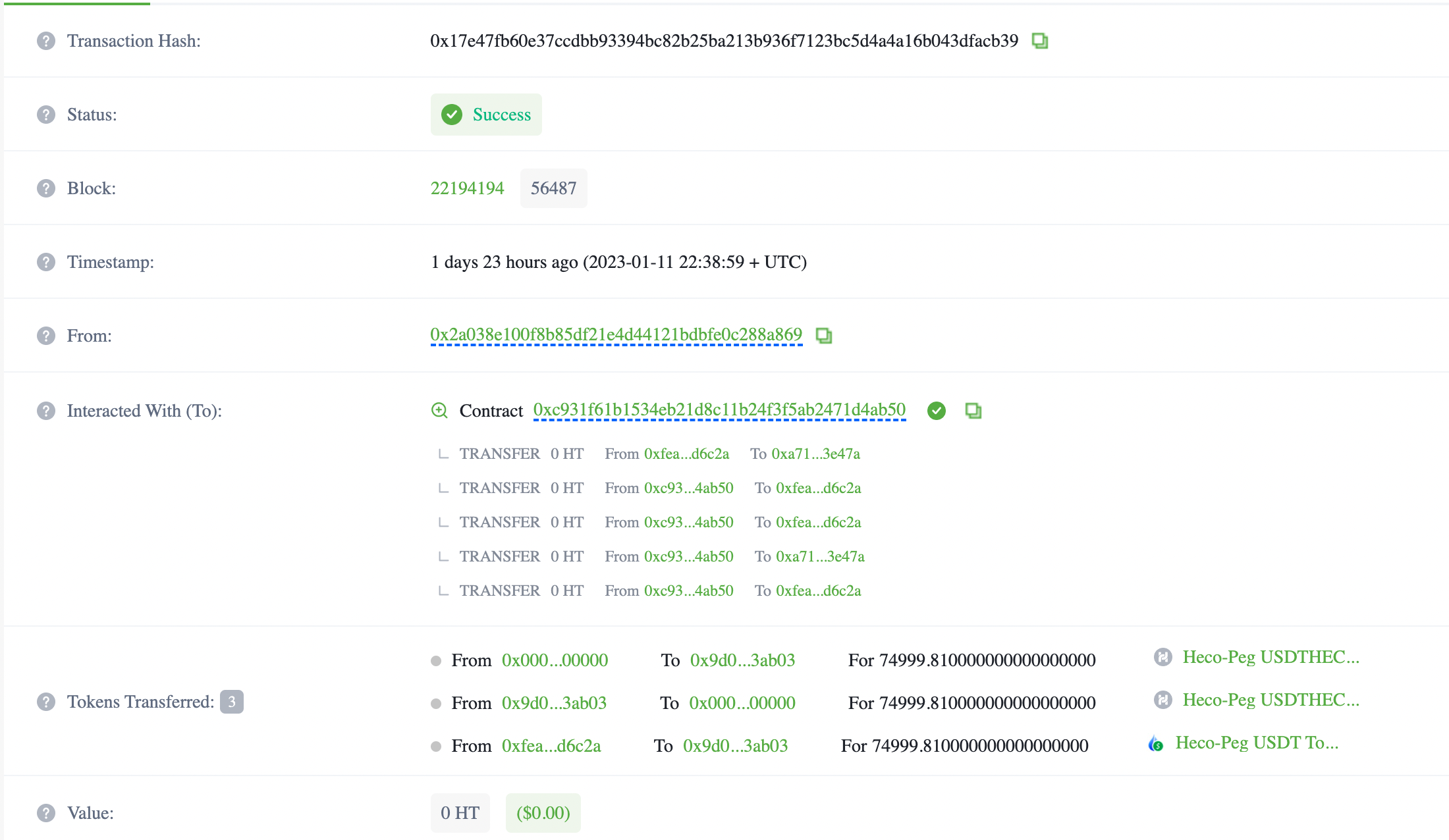 Image: Exploiter swapping ETH for HT and USDT Source: HecoInfo
Image: Exploiter swapping ETH for HT and USDT Source: HecoInfo
- The exploiter then interacted with the attack contracts multiple times, which drained assets from the new Lendhub HECO market. As an example we can look at the transactions coming from 0xfced6…:
a. Contract 0xafef5... deposited 659 HBSV tokens into the old HECO market (0xdf933…) and received 6,592,539,413,951 IBSV tokens in return.
b. Contract 0xafef5… then borrowed 2,106 HDOT tokens from the new HECO market (0x6371…).
c. Contract 0xafef5... transferred the deposited 659 HBSV tokens to the exploiter.
d. The exploiter then repeats steps a through c to drain HDOT tokens from the new HECO market.
e. Finally, the exploiter withdraws funds from the attack contracts.
Asset Tracing
The wallet used in the exploit is 0x9d016… which extracted 1,100 ETH (approximately $1.5 million) into Tornado Cash and currently holds around $2.7 million in DAI and USDT on Ethereum. Additionally, the exploiter’s Optimism wallet holds approximately $1 million in WBTC. Across HECO, Ethereum, Optimism, and the funds deposited into Tornado Cash, the exploiter is in control of $5,373,679.79 worth of stolen assets. As of writing 1,100 ETH (approximately $1.5 million) has been transferred to Tornado Cash and the exploiter still holds approximately $3.8 million.
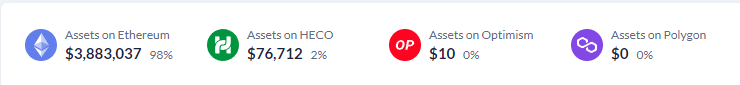 Image: Exploiter stolen asset distribution. Source: DeBank
Image: Exploiter stolen asset distribution. Source: DeBank
Conclusion
The exploiter transferred the stolen funds from LendHub to other chains like Ethereum and Optimism. After transferring the assets to Ethereum, the exploiter funnelled stolen funds into sanctioned cryptocurrency mixer Tornado Cash. Although the contracts were unverified, the vulnerability very likely stems from the fact that the old and new IBSV tokens existing simultaneously in the market and sharing the same price.
Smart contract auditing can recognize and neutralize incidents before malicious actors can exploit and steal funds. Protect yourself and your assets by following @CertiKAlert on Twitter to stay up to date on all the latest Web3 security news, and visiting CertiK.com as part of your due diligence.



